INTERNAL THREAT MANAGEMENT: IS YOUR DATA SAFE?
Protecting an organization and its data from…
Driving Change & Efficiency
through Modern Technology
Enhancing Human capabilities, improve efficiency, enhancing decision-making skills so on and so forth and drive innovation across various domains.

Infrastructure Services
that Leverage Your
Business to New Heights
Improving a company by boosting productivity, enabling scalability and flexibility, improving data management, optimizing costs, ensuring business continuity, enhancing security, improving customer experience and fostering innovation and agility.

Bringing about Success
through Strategic IT
Consulting and Execution
Expert guidance, strategic planning, and hands-on approach to implementation of technology solutions to help businesses achieve their goals.

Guiding Your Business
Towards Strategic Success
Keeping up with technology and capitalizing
on the huge potential provided by technological innovation.
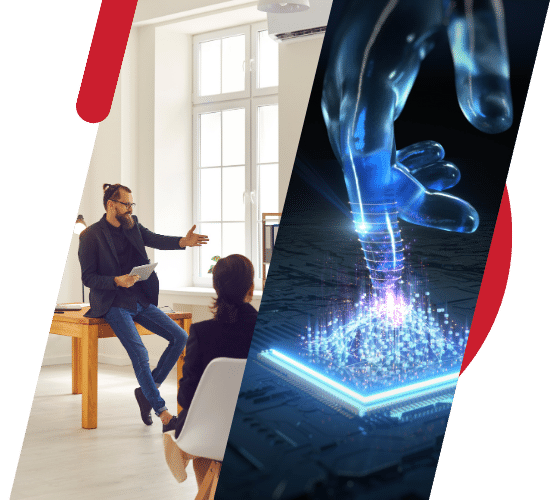

At Mericas, we believe that technology is the backbone of every successful business. With a team of highly skilled professionals and years of industry expertise, we are dedicated to providing top-notch IT consulting and services tailored to meet your unique business needs. Our commitment to excellence and customer satisfaction sets us apart as a reliable partner you can trust.

At Mericas, we offer a wide range of IT services designed to streamline your operations, enhance productivity, and drive innovation. Whether you need assistance with network management, cybersecurity, cloud solutions or software development we have you covered. Partner with us to embark on a transformative journey that will propel your business towards sustained growth and success.

At Mericas, we are at the forefront of driving technological transformation across diverse industries. With our innovative IT solutions and deep industry expertise, we empower businesses to thrive in the digital age.










They are a valued partner who offers intellect, vision, strategy, action steps, all with encouragement and keeping myself accountable to the next steps of my business.

5 R Process
Protecting an organization and its data from…
Protecting an organization and its data from a breach or attack can be a daunting task to undertake. There is such a wide range of possible dangers that preventing risks from evolving into active threats is not one job, but a variety of measures, tools, and practices put in place. While preventing attacks from external sources might seem hard enough on its own, it is vital not to forget that threats can come from within an organization as well. Whether they are the result of malicious, negligent, or compromised insiders, internal threats can pose a major danger to a business and its assets. An insider threat occurs “when an organization’s trusted users abuse or misuse their access to sensitive information and assets.” Each person with authorized access to any part of an organization – digital or otherwise – is an insider with the potential to cause damage. This includes not only employees, but contractors, partners, custodial workers, repair people, and anyone else who is granted access to the organization’s network, resources, or assets. The most prominent concern is data leakage, as insiders with access to sensitive enterprise data may, either through their intentional or unintentional actions, allow that data to fall into the wrong hands. There are essentially three different types of insider threats. The first is a malicious insider who, for one reason or another, has chosen specifically to cause damage to their organization from the inside. This is often done for financial gain or personal vendetta, and it covers cases like employees stealing trade secrets to sell to competitors or taking client information when they leave a company. The second type occurs when an insider is either ignorant or negligent of cybersecurity policies and practices and, through action or inaction, accidentally poses a threat. The last type is the compromised insider, which is an external actor gaining access to an insider’s account through phishing or hacking and then using that account to further infiltrate the company.
Windows Server 2012 and Windows Server 2012 R2 will end on October 10, 2023. This means that after this date, these products will no longer receive security updates, non-security updates, bug fixes, technical support, or online technical content updates. Additionally, on January 14th, 2020, Microsoft ended extended support for Windows Server 2008 and Windows Server 2008 R2. If your business is running Windows Server 2008 or Windows Server 2008 R2, you’re at risk of your applications and servers no longer fulfilling their business objective. Assess Your Options for 2012 workloads Move to Azure Move apps and workloads to Windows Server and SQL Server on Azure Virtual Machines Run securely with free Extended Security Updates for three more years after the deadline for Windows Server 2012 and 2012 R2 and SQL Server 2012 . Save with Azure Hybrid Benefit. Modernize when ready Modernize to PaaS with Azure services such as App Service, and Azure SQL Managed Instance. Never have to patch or upgrade again ~ OR ~ Upgrade On-Premises Upgrade to the latest version Windows Server 2022 SQL Server 2019 Can’t meet the deadline? Protect server workloads
Virtual learning, a key component of most cybersecurity awareness training programs, uses web-based platforms to allow employees to complete their training anytime, anywhere in the world. Many regulatory bodies already mandate cybersecurity awareness training and require organizations to prove their staff has achieved competency to comply. This article will examine the most significant regulations and how organizations can comply. see it herehttps://www.universaljewelersmfg.com/about-usinvestigate this site A key component of most cybersecurity awareness training programs, uses web-based platforms to allow employees to complete their training anytime, anywhere in the world. Many regulatory bodies already mandate cybersecurity awareness training and require organizations to prove their staff has achieved competency to comply. This article will examine the most significant regulations and how organizations can comply.


At Mericas, we offer a wide range of IT services designed to streamline your operations, enhance productivity, and drive innovation. Whether you need assistance with network management, cybersecurity, cloud solutions, or software development, we have you covered. Partner with us to embark on a transformative journey that will propel your business towards sustained growth and success.
5 R Process
We believe that technology is the backbone of every successful business.
2025 All rights reserved by Mericas.com